What Is Identity Management Software?
Identity management software enables organizations and individuals to effectively administer their identity management processes. An identity management process is designed to identify, authenticate, and authorize individuals to access organizational software resources.
’Identity Management‘ (IdM) software helps the administrators of an organization to clearly define and modify a person’s role in the organization and authorize the relevant access to them. This software also enables administrators to track users’ login and activity on the organizational computer network. This enhances operational security.
The Importance Of Identity Management Software
Most organizations, whether a business, a government organizations or a non-governmental organizations (NGOs), work in an environment characterized by stringent data privacy regulations. Some sectors like healthcare and financial services have even high regulatory compliance requirements.
Given this context, an IdM is very important, due to the following reasons:
- It helps in governing and managing the overall IAM program in the organization.
- Records from the IdM software enable organizations to assess their IAM effectiveness.
- The software makes it easier to administer IdM, access management, limit access to sensitive IT assets, etc.
- Analytics from the IdM software helps organizations strengthen their IT security practices.
What are the challenges that exist in the traditional identity management system?
The present identity management system faces the following four major challenges:
- Identity theft
- Combination of usernames and passwords
- KYC onboarding
- Lack of control
Identity theft
People share their personal information online via different unknown sources or services that can put their identification documents into the wrong hands. Also, as online applications maintain centralized servers for storing data, it becomes easier for hackers to hack the servers and steal sensitive information. According to the Breach Level Index, 4,861,553 records are stolen every day, accounting for:
- 202,565 records every hour
- 3,376 records every minute
- 56 records every second
The breach statistics indicate how quickly a hacker can steal personal or other confidential information.
A combination of usernames and passwords
While signing up on multiple online platforms, users have to create a unique username and password every time. It becomes difficult for an individual to remember a combination of usernames and passwords for accessing different services. Maintaining different authentication profiles is quite a challenging task.
KYC Onboarding
The current authentication process involves three stakeholders, including:
- verifying companies/KYC companies
- users
- third parties that need to check the identity of the user
The overall system is expensive for all these stakeholders. Since KYC companies have to serve requests of different entities such as banks, healthcare providers, immigration officials, etc., they require more resources to process their needs quickly. Therefore, KYC companies have to charge a higher amount for verification, which is passed to individuals as hidden processing fees. Moreover, third-party companies have to wait for a long time to onboard the customers.
A global survey of “Know Your Customer” challenges found that global annual spending on KYC is estimated as the US $48million.
Lack of Control
It is currently impossible for users to have control over personally identifiable information (PII). They do not know:
- how many times PII has been shared without their consent
- where all their personal information has been stored
As a result, the existing identity management process requires an innovative change. Using blockchain for identity management can allow individuals to have ownership of their identity by creating a global ID to serve multiple purposes.
How Can Blockchain Help With Identity Management?
Blockchain offers a potential solution to the above challenges by allowing users a sense of security that no third party can share their PII without their consent.
By using blockchain:
- A platform can be designed to protect individuals’ identities from breaches and thefts
- People can be free to create self-sovereign and encrypted digital identities
- The need for making multiple usernames and passwords can be removed
Blockchain technology promises to make identity management better due to its following characteristics:
- It is decentralized and therefore doesn’t require a central authority to control the data. This is true with Bitcoin and the Ethereum network.
- Using modern cryptography consensus algorithms helps with securing data.
- The immutability of records facilitates trust.
- Smart contracts are immutable pieces of code that can autonomously uphold contractual terms and conditions, with irreversible outcomes.
How does the blockchain identity system work?
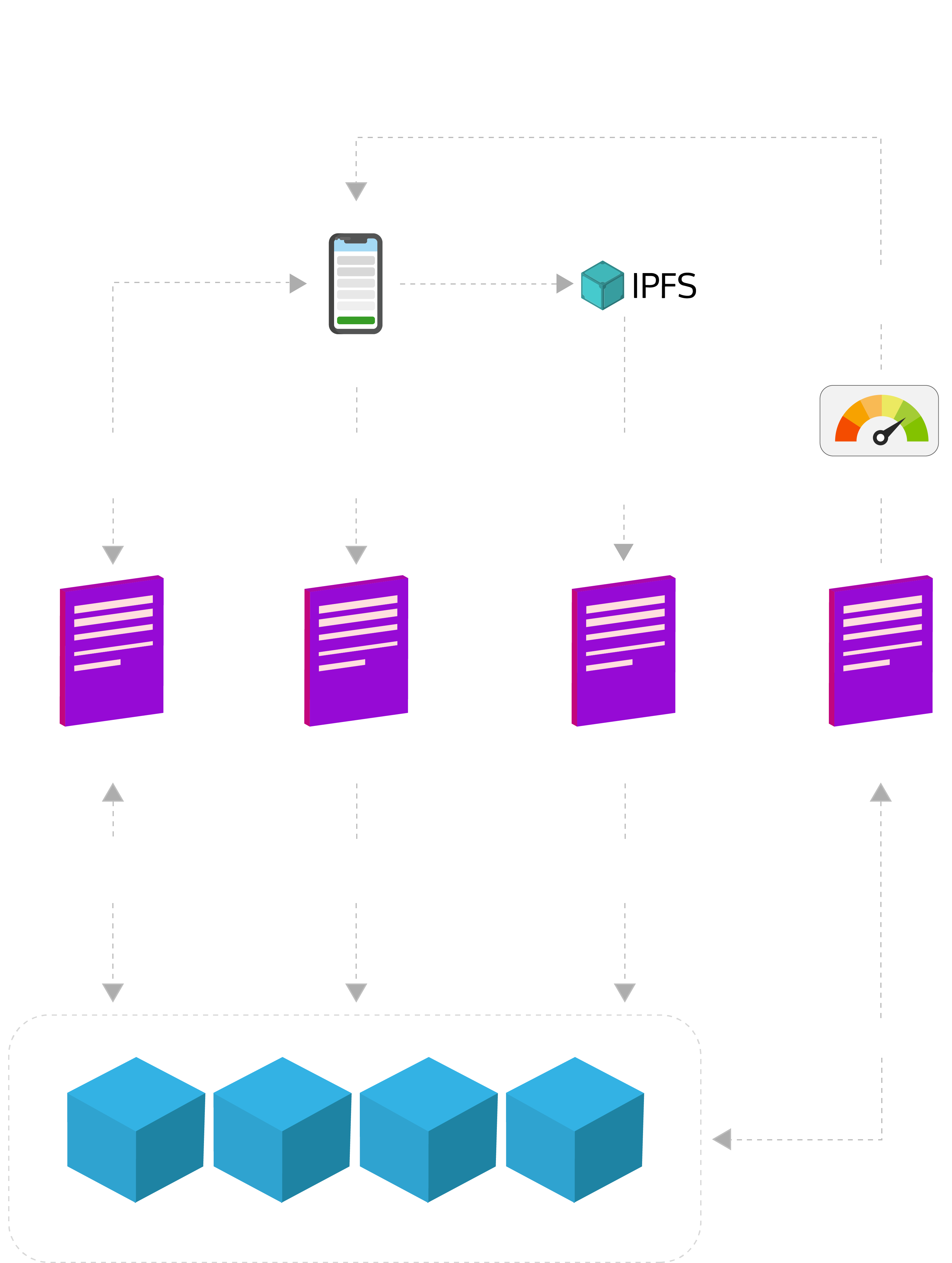
To understand how a blockchain identity management system works, we should know about the technical components involved in the process.
There are five technical components and interfaces that could be involved in the Blockchain based Identity Management Process:
- Native Android/iOS App for individuals.
- Native Android/iOS App for third-party companies/verification companies.
- Inter-Planetary File System to store the user’s PII.
- Microservices programmed using Node.JS.
- Permissioned Blockchain Component.
What are the benefits of the blockchain identity management system from the user’s point of view?
From the user’s point of view, there are four benefits of using blockchain identity management:
- Unique ID
Each user who registers on the blockchain identity management system will get a unique identity number. The user’s unique ID number consists of all personally identifiable information in an encrypted format stored on their device backed by IPFS. Users can share unique IDs with any third party to authenticate themselves directly through blockchain identity management. - Consent
A blockchain identity management system will not store any user’s information. Moreover, the system uses smart contracts to enable controlled data disclosure. Thus, data manipulation is not possible on the blockchain. An identity management system linked with blockchain is highly secure for identity holders as well. No transaction of the user’s information can occur without the explicit consent of the user. It makes the user control their personally identifiable information. - Decentralized
No personal identification documents of the users will be stored in a centralized server. All the documents that identify users get stored on their devices backed by IPFS, making them safe from mass data breaches. Using the Blockchain identity management backed by IPFS doesn’t allow any hacker to steal identifiable information. Since the system will be decentralized, there will be no single point of failure (SPOF). A single point of failure represents that part of the system – if it fails, the system will stop working. Therefore, the absence of SPOF ensures that the system will never compromise. - A Universal Ecosystem
Blockchain identity management doesn’t set any geographical boundaries. So, users can use the platform across borders to verify their identity.
Successful implementation of Blockchain identity management can enhance the level of security and privacy. The immutable and decentralized ledger allows third parties to validate the user’s data without wasting time and money.