With the rise of tokenization and cryptocurrency adoption, — together with more professional and institutional entities entering the space— the question of how to store the keys that allow access to these digital assets is becoming increasingly important.
What is custody?
From a technical standpoint, custody is about safeguarding private keys, the cryptographic alphanumeric combinations needed to transfer and store digital assets. They are the single point of failure within the space — losing them means losing the respective holdings with literally no chance of recovery.
There are multiple custodial solutions, each offering unique benefits to the user. They range from self-custody with hardware or software wallets to third-party offline-storage, and everything in between. Some users need more frequent access to their assets as others. Some investors might require third-party cold-storage for legal and insurance reasons or because they are obliged to do so.
Types of Custody
1. Self-custody
There are multiple ways to self-secure private keys. One can use hardware wallets, printed paper wallets, or encrypted data stores. In the end, the keys are moved offline into a “safe” in possession of the owner of the assets. This leaves the applicant as the single point of failure for loss of access or compromise — there is no third-party involved in managing this risk.
2. Managed Custody (Multi-sig, MPC)
Those are products and solutions where a scheme is employed to not have a single point of failure (one human, one account, or one device) when storing and using the keys. It amounts to a form of split or partial custody where the customer names multiple roles/persons (authorised officers, notaries, lawyers) that are required to cooperate within the signing process. One can imagine this like every involved party only having “one chunk of the complete key”. The exact amount of control and scheme used can be defined by the customers needs, ranging from a 2-of-3 multi-signature scheme to complex legal arrangements between the involved parties.
How to protect keys in custody?
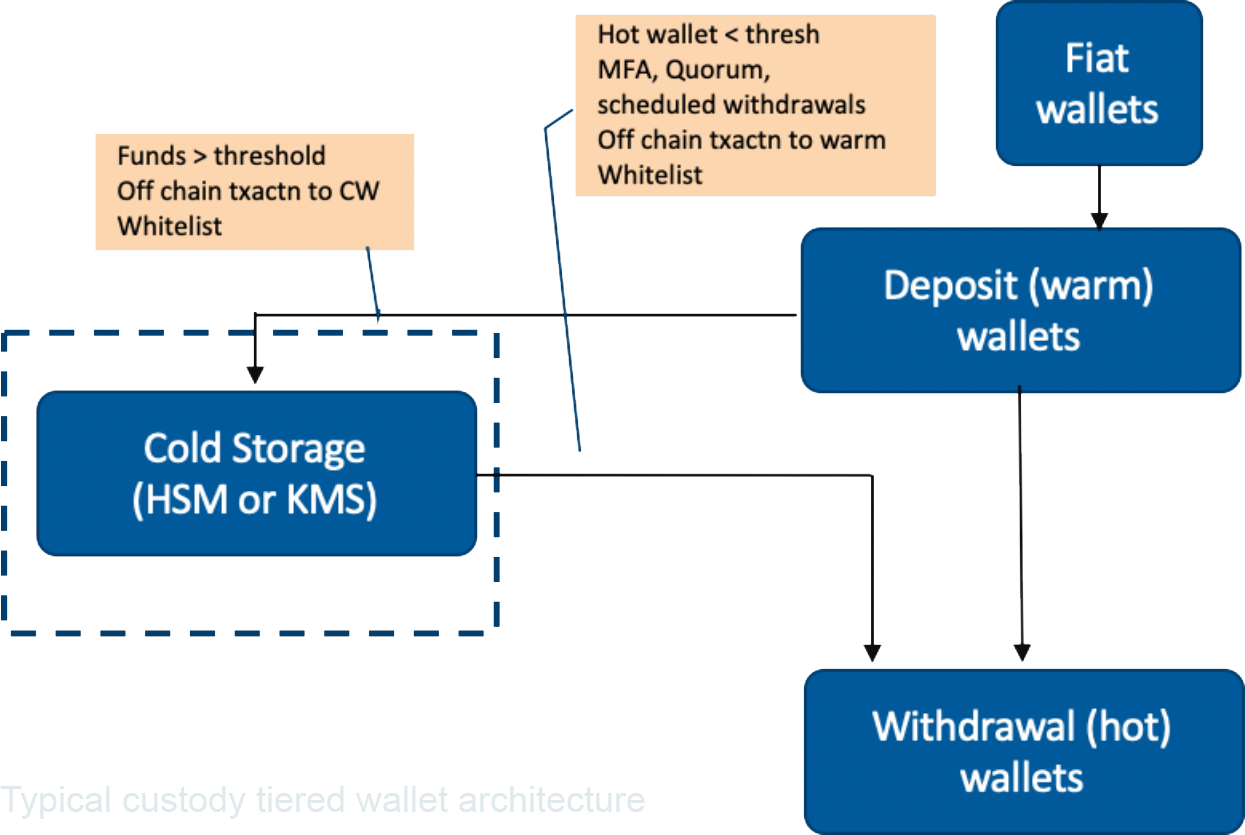
The most common approach to protect private keys for custody services is a tiered wallet architecture providing security through limited fund access. The tiered wallet architecture is a combination of hot and cold wallets to balance between making a portion of the funds in custody available online in a hot wallet for daily trading and securing a majority of funds off-line in a cold wallet. The objective of the cold wallet is to provide maximum protection against hackers, malicious insiders, or the risk of private keys being accidentally exposed to unintended parties.
1.1 Hardware Security Module (HSM) Approach
HSMs are specialized hardware appliances that are commonly used in the payments industry to store sensitive cryptographic key material and perform operations with those keys. HSMs incorporate true random number generators for strong key generation and provide physical safeguarding of the private keys during storage and while in use, and also ensure that the keys never leave the physical confines of the HSM. Each HSM is usually only accessible by authorized personnel or an optionally authorized quorum of personnel via secure and physical admin interfaces. The figure below depicts a typical custody wallet architecture with an HSM.
HSMs typically require a Key Management System (KMS) or other external applications to assist in managing the life cycle of crypto keys from the stages of key creation, distribution, maintenance, and eventually destruction of the key, as well as cryptographic operations. KMS brings some level of automation to the crypto operation for HSMs that helps to minimize human error and improve private key security compared to the DIY approach mentioned above.
1.2 HSM and MultiSig
For added security, most providers rely on multiple approver schemes like MultiSig to sign withdrawal transactions. MultiSig is not natively supported on HSMs and requires an external app or customization of the HSM. Through MultiSig, a minimum number of approvers are required to approve transactions using private keys assigned to each approver and based on policies associated with each approver. The most commonly used MultiSig scheme is 2 out of 3, meaning 2 signatures out of 3 potential approvers, typically requiring separate HSMs holding private keys to successfully sign a transaction. HSMs have been around for over two decades and are widely regarded as expensive and difficult to use.
1.3 Security Model
The key ceremony relies on processes, procedures, and those who ultimately manage the keys, key backups, hardware, and software authenticity. The manual process nature of the key ceremony came to be viewed as a security measure; however, it introduces a significant delay in making assets available for trading and liquidity. The use of manual key management processes, based on paper or cumbersome tools such as spreadsheets accompanied by manual key ceremonies, can easily result in human errors that often go unnoticed and may leave keys highly vulnerable. Furthermore, major security risks to the private key remain after the key is reconstructed, all secrecy and protections can be lost. As an example, a rogue insider can privately use other parties’ shares or use constructed keys to maliciously transfer assets in custody. Cryptocurrency custody solutions have made many advancements in securing digital assets using trusted individuals, processes and available technologies like HSM, MultiSig or opensource software as a core technology to secure crypto assets. Many of the challenges in securing such assets are rooted in lack of regulation and oversight, being vulnerable to hackers, and transactions being non-reversible. Some of the components of existing core technology were never designed to meet the challenges of securing virtual currency and despite many security advancements exchange thefts continue to be a significant problem.
Private Key Security
The most common model of private and public key generation for custody services requires a manual and/or quorum approval process that is typically human-managed, using an HSM or a ceremony operation. These private keys are secured as a whole key in an HSM or fragmented into multiple key shares and stored in USB or paper wallets if shares are generated through the key generation ceremony. Modern cryptography enables the use of ThresholdSig for key operations and provides the following security enhancements:
1.1 Distributed Key Generation
With ThresholdSig, there is no combined private key – instead cryptographic level private key shares are generated on MPC nodes which may run in a container, VM, or a mobile device environment. Ideally, these nodes are operated in different locations or in isolated networks to generate key shares and perform cryptographic operations. MPC nodes, through specific protocols, involve a set of “n” nodes for key generation and a subset “m” of the nodes to perform crypto operations, using a subset of key shares. Since key shares are distributed on each node, the private keys are never constructed or stored in one place offering enhanced key security and eliminating a single point of failure compared to legacy approaches.
1.2 Proactive Security
ThresholdSig offers a critical security feature referred to as key share refresh which emulate private key rotation by creating a new set of key shares without changing the corresponding public key and wallet address. Key share refresh increases security effectiveness and provides greater business flexibility when devices are lost, stolen, or hacked, as well policy-related changes triggered by adding or changing users associated with transaction approvals. Unlike MultiSig, ThresholdSig provides this enhanced security without requiring on-chain transactions or a change of the key address, so this is a major operational and security enhancement.
Private Key Recovery
The ability to retrieve a lost private key in order to execute a new transaction on blockchain is a complicated issue. Even Crypto-Exchanges failed to manage securely private key for their users. Too few wallets are trying to find a solution which could improve significantly user experience since users are already used to retrieve passwords if forgotten. Any UX designer would include a “Forget Password” link in a sign in page.
Security Problems & Loss of Private Keys
The loss or theft of private keys is detrimental. If a hacker gets hold of the private keys, they can transfer funds to an address only they control. If the keys are lost, assets can never be spent, rendering them useless. Therefore, lost or stolen keys equates to lost or stolen assets. Security risks only increase when assets are managed by organizations rather than individuals, as private keys need to be shared.
It’s easy to share keys — just hand over a copy, but impossible to unshare! If someone with the knowledge of the private key leaves the firm on bad terms or has hidden intentions, the organization is left exposed to potential theft and loss of their digital assets from the individual if they’re unable to move the assets off the addresses quickly. But even if the keys are not lost or stolen, assets can be still stolen as a result of fraudulent transactions.
Ideally, the keys are never exposed to users. Instead, transactions should be proxied through a custodian, who can apply controls to ensure that all approvals are gathered and all policies are satisfied, before the transaction is submitted to the blockchain.
For example, multisig controls allow both sharing of wallets in an organization, and approval workflows, e.g. 2 out of 3 employees must approve a transaction. Approval lists can control where the funds can be sent. However, given the almost infinite variety of required controls, it is important to work with a custodian who can support custom automated rules to ensure that any scenario can be accommodated for.
Basic Private Key Security Measures
Write – Copy your seed words carefully with a pen and paper, triple-checking it. Never store them online or electronically.
Confirm – Confirm correct copying with a test transaction, device wipe, and restore.
Copy – If wallet restore worked, make more copies of your seed words.
Hide – Hide these copies safely in different locations.
Laminate – For added security, laminate the paper copies and consider metal backups like Cryptosteel and Billfodl.