There is a strong misconception that the immutable nature of Distributed Ledger Technology (DLT) systems makes them inherently secure. However, there is a broad range of attack vectors targeting blockchain applications, targeting anything from cryptographic primitives to consensus mechanism vulnerabilities or smart contract exploits.
Overview
This blog covers the top ten attack types targeting cryptocurrency and DLT:
1. Exchange Hack
2. DeFi Hack
3. 51% Attack
4. Phishing (for private keys)
5. Rug Pull/Exit Scam
6. Ransomware
7. SIM Swap
8. Investment Scam
9. High Profile Doubler Scam
10. Extortion
1. Exchange Hack
With the average daily cryptocurrency exchange volume over $200 billion at the time of this re and the nascent nature of the industry, it is clear why so many hackers are drawn to targeting cryptocurrency exchanges.
- Phishing user credentials to gain access to cryptocurrency accounts and move money. These are sometimes combined with SMS hijacking to take over an SMS-based authentication code for a targeted user.
- Technical attacks against an exchange to penetrate the internal system, including:
- SQL injection attacks after an account have been created or accessed.
- Vulnerabilities in software used to operate the exchange.
- Unpatched software used by an exchange.
- Spear-phishing of employees at an exchange in order to override controls on withdrawals.
- Exploitations of API vulnerabilities to obtain stored credentials, such as private keys.
- Inadequate or incorrect use of cold wallets (offline storage of private keys) versus hot wallets.
- Insider threats have been common in exchanges.
- Decompiling exchange apps (iOS or Android) and discovering secret cloud API keys that are embedded in the app.
- Copying of wallet recovery keys.
- Attacks against specific currencies that exploit vulnerabilities in the exchange’s implementation of that currency.
2. DeFi Hack
It’s common for attackers to fund DeFi attacks through flash loans, which require no collateral or Know-Your- Customer (KYC) identification data, making it increasingly difficult to catch bad actors. While more decentralized exchanges are beginning to audit their contracts in the hopes of preventing an attack, vulnerabilities continue to be discovered by savvy hackers.
For example: On Feb 2, 2022, an unknown hacker exploited a vulnerability in the Wormhole Network, a popular cross-chain protocol, to carry out the second-largest theft from a DeFi protocol ever. Across a series of transactions, the hacker made off with roughly 120,000 Wormhole Ethereum (WeETH) worth over $320 million.
The hacker appears to have found an exploit in Wormhole’s smart contract code that allowed them to mint 120,000 Wrapped Ethereum on the Solana blockchain (known as Wormhole Ether or WeETH) without putting up the necessary equivalent Ethereum collateral.
To reduce the risk of DeFi Hack, while not foolproof, a valuable first step towards addressing issues like this could be for extremely rigorous code audits to become the gold standard, both for those building protocols and for the investors evaluating them.
3. 51% Attack
51% attack is an attack on a proof of work blockchain where a group of miners controlling more than 50% of the network’s mining hash use this power to prevent new transactions from being confirmed or to reverse transactions that were completed under their control, leading to a double-spend attack. Once this happens, there is often nothing written into the blockchain technology that can stop the attack. The biggest cost resulting from a 51% attack is the loss of confidence in the blockchain.
Mitigating a 51% Attack
Double-spends resulting from 51% attacks present security and confidence issues in blockchains. One way of improving security protocols and controls may be accomplished through exchanges. Some exchanges wait for a block depth of six confirmations before allowing the coins to be used, and this may be extended to a block depth of 30 or more confirmations once the blockchain informs the exchange that an attack is in progress. Its goal is to allow more time for the minority 49% of miners to regain the hash power of the blockchain and thwart theattack. This benefits the exchange as well— they won’t lose coins to double-spending.
4. Phishing (for private keys)
Phishing attacks are all too common in and outside of the blockchain economy. In a traditional phishing attack, criminals will “fish” for targets by casting a wide net and mass-emailing potential victims, posing as a legitimate institution to trick the reader into providing sensitive data such as usernames, passwords, banking and credit card details, and other personally identifiable information.
After the data leak on cryptocurrency hardware wallet provider Ledger, many buyers received spear-phishing emails that claimed the user needed to update their seed phrases using a provided link. However, doing so resulted in the attacker obtaining a copy of the user’s private keys, granting them complete control of all the cryptocurrency held by Ledger.
Common phishing attack vectors targeting cryptocurrency users include:
-
- – Spear-phishing emails posing as wallet providers or exchanges used by the target
- – Spear-phishing attacks by fraudulent groups and people on social media (Reddit, Twitter, Telegram) when seeking help
- – Unique phishing sites posing as legitimate crypto wallet providers and exchanges
5. Rug Pull/Exit Scam
In the crypto-verse, an exit scam refers to when an exchange disappears with user funds, seemingly out of the blue, leaving customers unable to withdraw from their accounts. This is typically the result of one or more members of the executive team misappropriating user funds and can be either planned from the inception of the exchange or happen suddenly due to inadequate safeguards to prevent embezzlement.
Rug pulls are similar to exit scams; both involve insiders taking off with a majority, if not all, of users’ funds. While often used interchangeably, exit scams are more often linked to established entities or projects unexpectedly closing down (“exiting”), taking user funds with them
A rugpull, on the other hand, is a specific type of exit scam that involves “pulling the rug” out from under investors (users) by selling the majority of the DeFi pool, thereby draining liquidity from a specific token. Rug pulls are often accomplished through intentional back doors written into smart contracts.
6. Ransomware
The rapid growth of ransomware-as-a-service operations like REvil, Netwalker, and Darkside has become a lucrative business for threat actors. These recent attacks against critical infrastructures prove that ransomware doesn’t only impact individuals.
Ransomware-as-a-Service (RaaS)
In RaaS operation models, the malware developers partner with third-party affiliates (hackers) who are responsible for gaining access to a network, encrypting devices, and negotiating the ransom payment with the victim.
Combating Ransomware
Blockchain analytics provide the critical cryptocurrency intelligence needed to trace ransomware actors. Only by working together through groups like Ransomware Task Force, who can counter these threat actors. It is crucial to not only trace ransomware proceeds to find and stop the operators, but also to harden systems and educate the public on how these compromises occur in order to properly mitigate disruption.
7. SIM Swap
In a SIM-swapping attack, hackers use social engineering—including stolen credentials purchased on dark markets—to deceive a telecom provider into transferring the victim’s phone number to a SIM card (physical or virtual) that they control. This is typically reserved for cases when a subscriber’s phone is lost or stolen. Once cybercriminals receive the phone number, they can use it to reset passwords and break into the victim’s accounts, including accounts on cryptocurrency exchanges
Protecting Against SIM Swapping
Users can reduce the impact of a SIM swapping attack by not using their phone numbers for two-factor authentication and two-step verification in which the second factor is an SMS or a call placed to a mobile phone.
Additionally, customers can call their phone providers and enable a separate PIN. For example: “All Etisalat/Du Mobile accounts are assigned a 4 digit PIN.
SIM swaps usually come in three major flavors:
- Social engineering
- Breaking into the computer of an entity (e.g., a cell phone kiosk at the mall) that has privileged access to port phone numbers. This has been done using phishing, physical attacks, etc.
- Insiders at cell phone companies simply selling SIM swaps to attackers.
8. Investment Scam
Investment scams are old scams simply dressed up in new clothing — Bitconnect is a good example. It’s simple: you buy Bitconnect coins (BCC) and then invest the Bitconnect coin via a hosted lending platform (Bitconnect.co). Other people borrow the Bitconnect coins, do something, and pay back the loan. On its surface, this does not sound overly fraudulent to the inexperienced investor.
Bitconnect claimed to return 1% per day, an impossibly high consistent return. This also indicated that anyone borrowing Bitconnect would need to pay at least 1% a day, which should be an immediate red flag —either you’re borrowing money from a loan shark or your investment risk is so high that you probably should not be borrowing money to engage in that high-risk activity.
Bitconnect turned out to be a Ponzi scheme (early investors are simply paid out
from later investors). As long as investments increase the Ponzi scheme will work, but at some point the pool of available investors will dry up or someone will determine it’s a Ponzi scheme (destroying investor confidence).
9. High Profile Doubler Scam
Bitcoin doubler scams are simple and commonly propagated over social media by criminals. Doubler scams promise new investors—typically under the guise of a prominent, high-profile individual—that by simply sending funds to a specific address they will be sent back double the funds they initially invested. These scams are typically time-sensitive, prompting a sense of urgency in its victims in hopes that they are less likely to think critically about the offer.
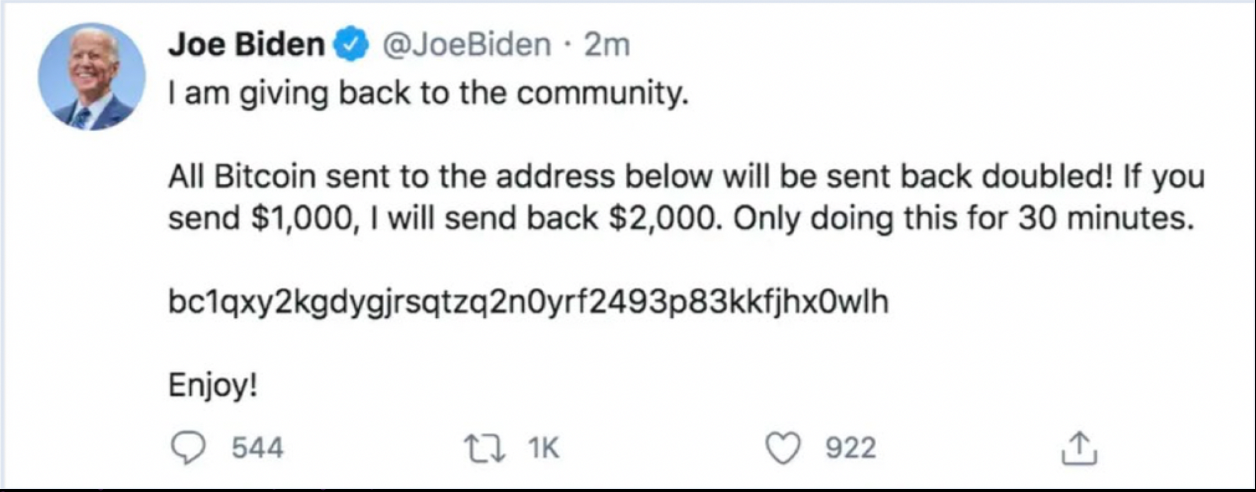
Mitigating Doubler Scams
This could be down to two main factors:
- Proper AML practices at exchanges which would prevent new users to transfer to fishy accounts.
- Creating more awareness
10. Extortion
Criminals are able to personalize their communications using data derived from breaches at Yahoo!, Experian, and Facebook to dupe email recipients into believing they have been recorded watching online pornography or involved in other compromising activities.
The scammers further claim to have collected the victims’ contacts and threaten to send the video to the list if the ransom, typically anywhere from a few hundred to a little over a thousand dollars worth of bitcoin, is not received.
A CipherTrace analysis of online extortion payment addresses has determined that most of these online extortion emails are fraudulent, but the emails are intimidating enough that even innocent victims may pay out of fear.
Preventing Extortion Attacks
More often than not, these extortion scams are fake—meaning paying or not will result in the same outcome: nothing. It is recommended not to pay extortions or reply to these emails.

