Over the last few months, we’ve seen a number of Web3 projects targeted by hackers using Web2 exploits to steal hundreds of thousands of dollars in user funds. There are lessons for other projects to be learned here. It’s worth taking a moment to reflect on these Web2 vulnerabilities so we can work together to safeguard the Web3 ecosystem.
Blockchain technology has revolutionized finance. Users have been able to directly manage their own money and investments thanks to self-custody, smart contracts, and Web3 products. But within this changing landscape, there needs to be a balance between decentralization and security. The latter is particularly important when regular people’s funds are involved. Given the decentralized nature of Web3, the focus is often on ensuring that the blockchain protocols and smart contracts at the heart of different products and platforms are robust, secure, and free from exploits.
However, many Web3 projects still lean on Web2 frameworks and technology to run additional functionalities on top of their core blockchain protocols. And so hackers are starting to use Web2 vulnerabilities as attack vectors when looking to steal project and user funds. One example is exploiting front-end code or systems rather than attacking the smart contracts themselves.
Here are some of Web2 vulnerabilities often overlooked within the Web3 projects
- Insufficient Authentication Controls
- Cross-Site Scripting (XSS)
- Phishing
- Platform – APIs, Web App Interfaces
- Payment Gateway Integrations
Web2 vs Web3: Major Security Differences
Web3 faces many of the same security risks as Web2. However, the differences between the two technologies create new security risks and amplify others. Below, we’ve outlined some of the main security implications of Web3.
- Patching vs Preventing
- Identity Management
- System Centralization
- Transparency vs Security via obscurity
What are these Web2 exploits? How do they work? And what can be done about them? Let’s look at a recent API exploit on FTX platform — and draw some conclusions from the example to help the wider community keep safe.
FTX users lose millions to 3Commas API exploit
Inconsiderate crypto hackers persist during the crypto winter. The recent breach on FTX resulted in the loss of millions of dollars worth of crypto. Hackers gained access to a crypto trader’s FTX account by exploiting an API tied to the account’s trading platform.
The automated crypto trading bot company 3Commas issued a security notice following the attack. 3commas took action after detecting certain FTX API keys used to conduct illicit transactions for DMG crypto trading pairs on the FTX exchange.
FTX API exploited
A user first discovered that his account was trading DMG tokens more than 5,000 times before the hacking complaints surfaced. The customer afterward learned that over $1.6 million worth of Bitcoin, FTX token, Ethereum, and other cryptocurrencies had been stolen from their account.
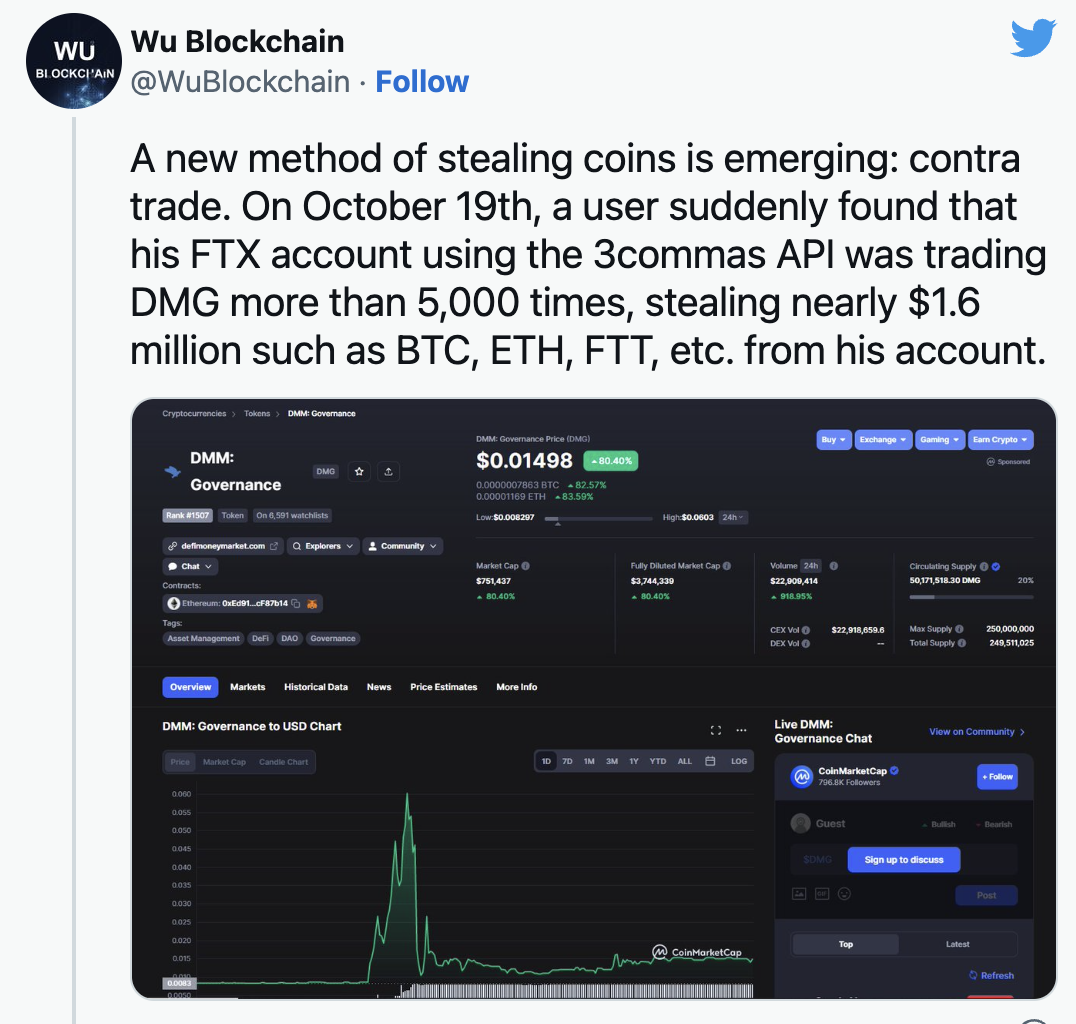
Reports indicated this was not an isolated incidence, as there were three more victims. On its part, FTX said that the hack was related to the leakage of the API keys for the trading platform 3Commas.
Bruce, a second FTX user, revealed in an October 22 Twitter thread that he was a casualty of the FTX attack. He disclosed that he lost $1.5 million as a result of the October 21 incident. According to Bruce, he has never used or even heard of the 3Commas punctuation mark. In addition, I had never used the API key in the previous two years. I had never recorded the secret on paper.
In addition, he reported that on October 18th and 19th, malevolent players traded DMG using his account. He questioned why FTX had no risk management procedures in place for illegal trading.
Exploit analysis
3Commas and FTX performed a collaborative investigation into user claims of fraudulent trades using DMG trading pairs on FTX. The duo determined that the DMG trades were conducted using new 3Commas accounts and that “the API keys were not obtained from the 3Commas platform but from outside of it.”
The investigation revealed that fraudulent websites posing as 3Commas were used to phish API keys from users as they joined their FTX accounts. The FTX API keys were then utilized to conduct the illegal DMG trades. Based on user activity, both FTX and 3Commas identified suspect accounts and stopped the API keys to prevent future losses.
3Commas also suspects API keys were stolen from users via malware and third-party browser extensions. In addition, 3Commas denied responsibility, stating several affected users have never been 3Commas customers and there is no chance the security incident originated with 3Commas’ services.
FTX users who have connected their accounts with 3Commas and have received a notification that their API is “invalid” or “needs upgrading” must generate new API keys. The trading-bot platform emphasized throughout the security notice that it was not responsible for customer data getting into the wrong hands.
Web3 offers a huge amount of opportunity, but we shouldn’t ignore security threats that have been there since the previous era of the internet. Let’s be vigilant and safeguard our ecosystem together on all fronts.

