As decentralized applications and smart contracts gain prominence, so do the threats posed by malicious actors. Unlike traditional web applications, data in Web3 is stored on the blockchain’s immutable ledger, making it virtually irreversible if an attack occurs. Additionally, the open-source nature of many Web3 applications provides opportunities for attackers to scrutinize code for vulnerabilities and plan exploits in advance. To address these challenges, a robust web3 security stack is essential, comprising different layers of protection.
Understanding the Web3 Security Stack:
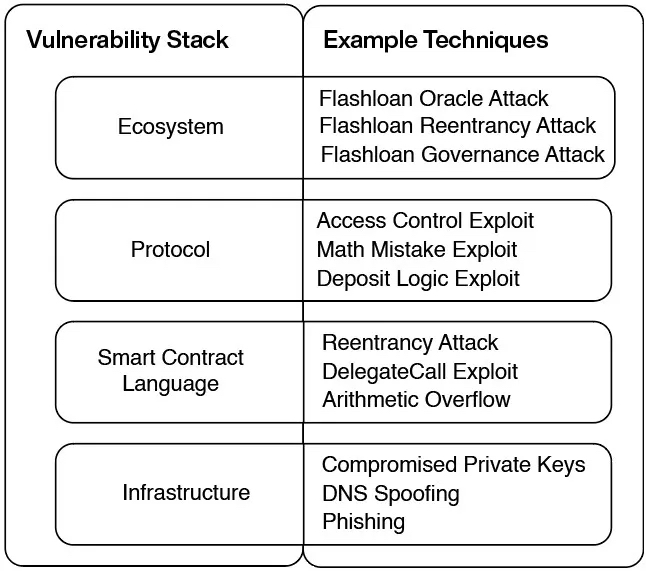
The web3 security stack can be categorized into four layers:
- Infrastructure: This layer focuses on identifying potential security threats during the system design phase. It involves selecting the appropriate blockchain protocol and ensuring secure interactions with the underlying blockchain. Key components include wallet and private key management, access management, consumer security, and monitoring & observability.
- Smart Contract and Protocol Logic: During the development, testing, and deployment phase, this layer aims to ensure the security of smart contract code and protocol logic. It includes security testing tools, formal verification, audit service providers, and bug bounty platforms to discover and fix vulnerabilities.
- Ecosystem: Once deployed to production (mainnet), this layer involves monitoring smart contracts and critical components for suspicious activity. It encompasses protocol risk management, threat intelligence, and blockchain forensics for real-time monitoring, incident forensics, and emergency response.
Let’s dive deeper into each layer of the web3 security stack:
Infrastructure Layer:
- Wallet & Private Key Management: The adoption of cryptographic wallet security solutions like multi-party computation (MPC) helps eliminate the risk of storing private keys in one place. Companies offer MPC wallet infrastructure to enable secure transactions across multiple chains.
- Access Management: Ensuring the secure authentication and verification of users or wallet accounts is essential. Developer tooling is available to automate permissions and control access to wallets and smart contract capabilities.
- Consumer Security: Emerging solutions provide protection against fraudulent transactions, hacks, scams, and theft. These platforms integrate with blockchain wallets to detect and prevent unauthorized activities.
- Monitoring & Observability: Platforms continuously analyze the health, reliability, and uptime of the underlying infrastructure services powering web3 applications, helping developers identify potential issues.
Smart Contract and Protocol Logic Layer:
- Security Testing Tools: Static analysis frameworks and bug-hunting engines help developers detect vulnerabilities in smart contracts and codebases.
- Formal Verification: Using algorithmic logic to check smart contract properties, this process ensures the security and correctness of code before deployment.
- Audit Service Providers: External security assessments detect and describe security issues and vulnerabilities, offering recommended fixes.
- Bug Bounty Platforms: Incentivizing security researchers to discover and disclose vulnerabilities, bug bounty programs are crucial for open-source projects.
Ecosystem Layer:
- Protocol Risk Management: These solutions automate risk management and optimize protocol performance against extreme market conditions.
- Threat Intelligence: Data collection and analysis help understand cybercriminal motives and attack behaviors, generating alerts to prevent security threats.
- Blockchain Forensics: These processes and technologies investigate and contain cybersecurity threats impacting blockchain networks and web3 applications.